If your job is to manage cybersecurity for your company, you must fend off cyberattacks, prevent data breaches, and keep your network operating at peak productivity.
So your job is really about creating cyber resilience for the company.
What’s the difference between cybersecurity and cyber resilience?
Cybersecurity is the practice of deploying people, processes and technology to protect organizations like yours.
Cyber resilience evaluates how well an organization can do business during a breach or cyberattack.
How can you be proactive so your company is cyber resilient?
To be sure you are able to recover as quickly as possible and mitigate a disaster, you need to have a backup plan in place that works effectively for your organization.
Not only that, but you absolutely need people and processes ready to make your backup and recovery tools actually work.
There are three types of backups to look at:
Full backups are a complete copy of your organization’s entire data assets, which captures all of your files in one version.
![]() Pros
Pros
 Cons
Cons
An incremental backup is a backup that covers all files that have changed since the last backup, regardless of the backup type.
![]() Pros
Pros
 Cons
Cons
A differential backup is a cumulative backup, regardless of the backup type. If you do a full backup on Friday, and a differential backup on Monday, the differential backup would include all files changed between Friday and Monday.
![]() Pros
Pros
 Cons
Cons
Recovery is literally the process of retrieving and restoring all that backup data to your systems to mitigate downtime. Reliable backups and speedy recovery plans give businesses continuity and resilience in the event of a threat.
And of course, backup and recovery is not a “one-off.” It’s a continuous process that protects your organization if it is attacked.
Why wouldn’t you do the same with your other tools and processes?

Your blue teams and red teams need to continuously train in real-life scenarios, so they are aware of the cyber threat landscape. The most effective place to do that is a cyber range.
A cyber range is a training simulation platform that provides hands-on practice to cybersecurity professional teams, and perhaps those training to become cybersecurity professionals.
Cyber ranges can:
Your cyber responders need hands-on and specialized training education and training. The cyber range is a valuable tool and yet can be a fun, engaging way to learn.
In general, organizations seeking cybersecurity education, workforce development, training or skills lack simulated environments found in other professional industries, such as flight simulators for pilots in aerospace.
Cyber ranges provide a safe, legal environment to gain practical cyber skills in a secure workspace for product development and security-posture testing. Cyber ranges can and must play an essential part in facilitating and advancing cybersecurity education, training and certification.
Red teams can use cyber ranges to simulate attacks, so they can find and fix vulnerabilities before hackers exploit them, and perform counterattacks. This gives penetration testers (pen testers) a safer way to gauge the organization’s security than wait for an actual attack.
Blue teams in the security operations center (SOC) also have a variety of needs for and benefits associated with using a cyber range, which include:
Cyber ranges let SOC teams discover and incorporate IoCs based on better detection mechanisms and improved software solutions, along with stronger research, which have been learned through unique scenarios demonstrated on cyber ranges. This data can be shared with the wider information security community and help identify attacks or which cyber threat actors would be responsible.
Cyber ranges help SOC teams learn to better respond to SIEM alerts by triaging particular actions that would snuff an attack before it can spread deeper into the network. These actions are usually guided by a lot of trial and error, until the course of action is determined.
Cyber ranges allow SOC teams to practically learn the operation of their security solutions and spot unique areas of weakness for improvements. Based on their discoveries, SOC teams can update modular solutions to improve their functionality and make them more powerful. When these solutions are applied to real situations, SOC teams can get high performance and accurate results. This can greatly improve the chances of a successful mitigation.
Cyber ranges help blue team members learn documentation skills. Reports can be tweaked to be more easily understood in case they need to be escalated to another cybersecurity team, and for future reference. These documents can be important when examining a breach or when taking steps to contain security issues.
Cyber ranges can also teach SOC team members how to preserve evidence for forensic teams. This ensures multiple teams can work with the evidence.
Now that we’ve looked at how red and blue teams can improve with cyber ranges, let’s look at what a cyber range can do for the organization itself.
Using a cyber range, like Cympire’s CyWARIA, significantly increases an organization’s cyber resilience through continuous training and assessment, which mitigates the risk of a detrimental attack.
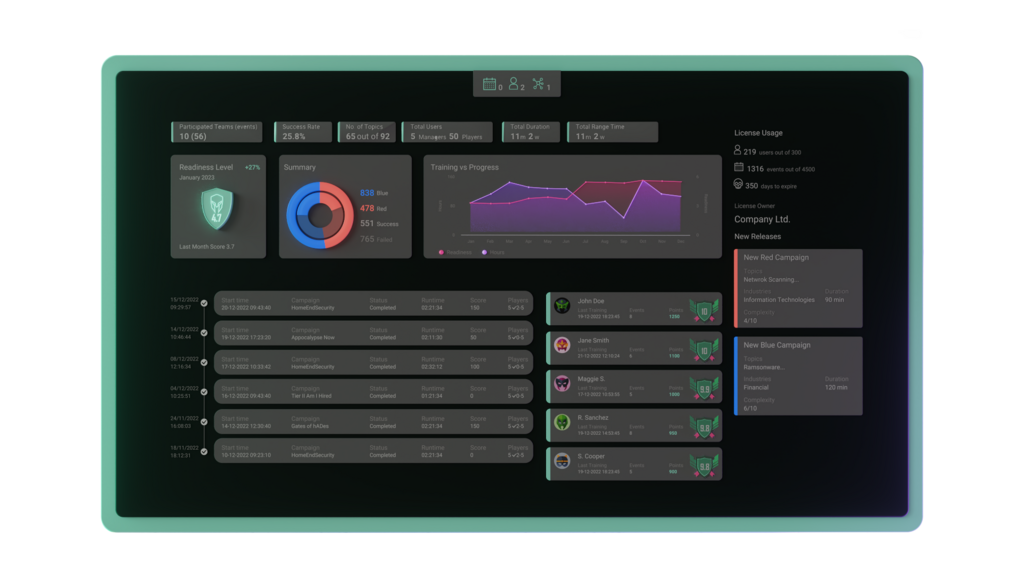
Use your cyber range as an assessment tool
CyWARIA cyber range allows companies like yours to:
Unlike its competitors, CyWARIA is:
Get a DEMO today!