The cybersecurity landscape is evolving rapidly, and organizations are increasingly relying on hands-on simulation environments to prepare analysts for operational challenges. Cyber ranges allow defenders to practice investigation, incident handling, and analytical decision-making in realistic yet controlled environments.
Beyond building individual expertise, simulation-based training also contributes directly to organizational resilience. Continuous practice helps teams improve their ability to interpret complex telemetry, work effectively under pressure, coordinate during incidents, and contain threats more rapidly. As a result, many organizations now treat simulation as an essential component of maintaining operational readiness.
Despite these benefits, one practical challenge persists. Although trainees participate in numerous exercises, it is often difficult to determine which competencies are being developed and how these experiences relate to defined professional roles.
At the same time, the NICE Workforce Framework (NICE 2.0) provides detailed definitions of the knowledge, skills, and tasks associated with cybersecurity roles. The framework includes approximately 540 individual micro-skills, designed to support standardization, job profiling, and workforce development. However, the level of granularity that makes NICE valuable also creates difficulty when applying it to practical training.
it becomes challenging to track progress or ensure that training aligns with the competencies required in practice
Instructors and learners often struggle to identify which subset of these hundreds of skills matters most for a given role, or how to structure a sequence of exercises that meaningfully supports role readiness. Without an intermediate layer of abstraction, it becomes challenging to track progress or ensure that training aligns with the competencies required in practice.
This gap between comprehensive skill taxonomies and hands-on simulation highlights the need for a practical model that preserves the integrity of the NICE Framework while translating its extensive skill set into a manageable structure that supports measurable training.
To bridge this gap, At Cympire we have built a systematic mapping between cyber-range scenarios and the NICE Framework through an intermediate layer of capability clusters. These clusters represent functional domains commonly engaged in day-to-day defensive operations, such as Network Analysis, Endpoint Analysis, Monitoring & Detection, and Vulnerability Assessment. Each capability cluster consolidates multiple NICE micro-skills that share thematic or operational similarity. For example:
By grouping the 540+ micro-skills into a coherent and concise taxonomy, the model makes it easier for both trainers and learners to understand what each scenario strengthens, while maintaining traceability to the underlying NICE definitions.
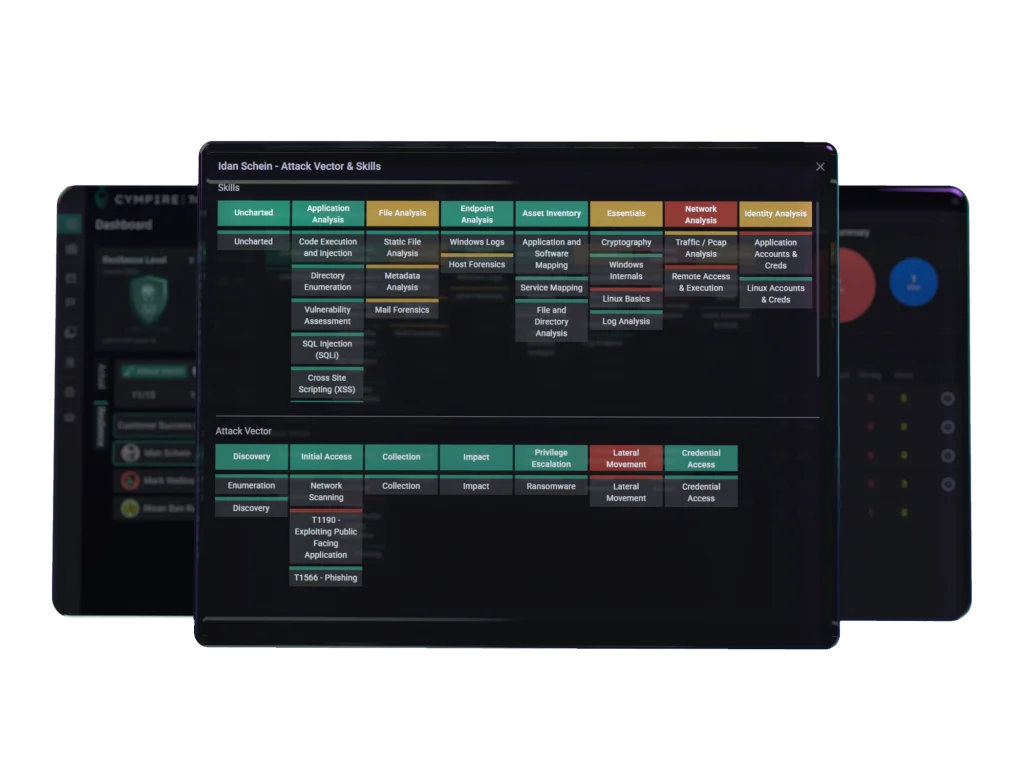
With capability clusters defined, each scenario in the cyber range is analyzed and tagged according to the primary analytical or investigative actions it requires from trainees. This allows for a consistent and repeatable approach to understanding the skill implications of each exercise.
Examples include:
This structured mapping enables several operational advantages:
The model becomes particularly effective when applied to role-specific development.
Consider the NICE role PD-WRL-001, responsible for analyzing data collected from cybersecurity tools to mitigate risks. This role emphasizes capabilities such as Network Analysis and Monitoring & Detection.
By examining the NICE skills associated with PD-WRL-001, the system identifies the capability clusters most relevant to the role and prioritizes scenarios that reinforce them. This creates a structured learning path that progresses from foundational analytical tasks to complex, multi-step investigations.
The result is a training experience that is:
Because scenarios are tagged to capability clusters, which in turn are mapped to NICE micro-skills, training outcomes can be evaluated from multiple angles:
This enables organizations to shift from activity-based reporting (“X scenarios completed”) to competency-oriented evaluation (“Y% of role-required skills demonstrated under realistic conditions”).
Hands-on simulation is essential for developing and maintaining cybersecurity proficiency at both the individual and organizational levels. However, without a structured method for connecting simulations to recognized frameworks, training outcomes remain difficult to quantify.
The capability-cluster approach provides a practical bridge between hands-on exercises and the NICE Framework. By consolidating hundreds of micro-skills into operational clusters, mapping scenarios accordingly, and enabling role-aligned progression and analytics, organizations can create training programs that are measurable, targeted, and aligned with real defensive responsibilities.
This structured model supports more effective skill development, clearer progress tracking, and greater overall resilience — helping defenders advance from foundational proficiency to full operational readiness.
Cympire is a cloud-native, AI-powered cyber training and simulation platform that delivers scalable, live-fire exercises for military, government, enterprise, and education. With a catalogue that goes from theoretical blogs all the way to complex challenges tailored to diverse cyber positions (red teamers, blue teamers: SOC, IR, threat hunters and so on), every mission aligns with both MITRE attack and NICE 2.0 frameworks to ensure realism and relevance, while an NLP-driven AI Agent curates personalized training experiences in seconds. With its patented Cyber Range-as-a-Service (CRaaS) Cyber Studio, users can rapidly build and deploy custom, cloud-based environments—making cyber readiness training faster, smarter, and mission-focused.